NetRise Trace Behind the Scenes: How it Works
Following the release of NetRise Trace, our innovative, first of its kind AI-powered semantic search engine within the NetRise Platform, we want to provide some behind the scenes insight into the methodology and machine learning magic powering this advancement. As a solution provider seeking to enable visibility into the black boxes running within Extended Internet of Things (XIoT) devices, it’s only right that we should be as transparent as possible with our own processes — especially when it comes to notoriously opaque aspects like AI and ML.
Extraction
It all starts with our proprietary extraction engine, tailored for dissecting a variety of complex software file formats covering things like firmware, standalone software packages, docker images, virtual machines, bootloaders, ISOs, and more. When firmware or other files are fed into our system, the first step is a journey through our cloud-based extraction engine, revealing nested file formats. This approach, often referred to as binary analysis, is far superior to SCA when looking for a complete picture of the components and files within firmware.
Let's look at how it works with some Cisco firmware. You can see we are able to extract the files and underlying components that were used to create the firmware.
Components
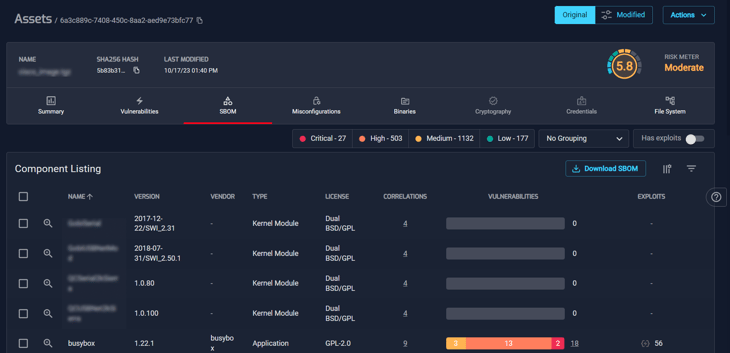
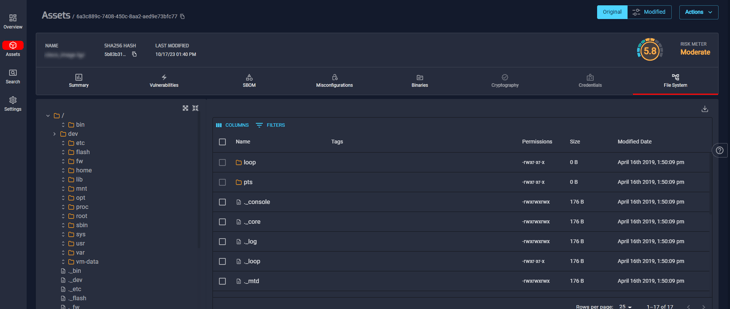
Recreated File System
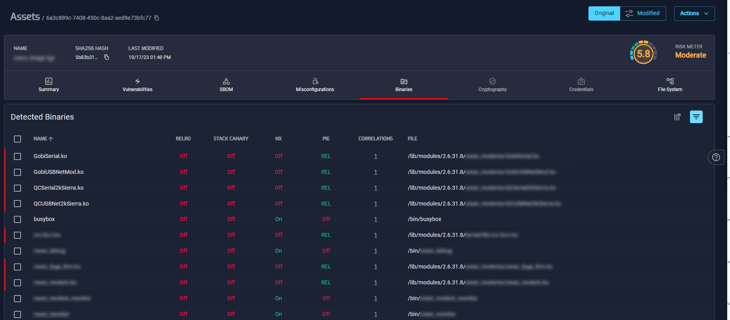
As well the binaries
Analysis
The NetRise Platform leverages AI in the form of NLP (Natural Language Processing) to create high-dimensional vectors representing the semantic meaning of the chunks of extracted data. This is sometimes referred to as creating text embeddings, a NLP technique that converts textual data into numerical vectors that can be processed by machine learning algorithms, especially large models. These vector representations are designed to capture the semantic meaning and context of the words they represent and ultimately enables this new form of search to operate.
Querying the Data
Users can input search queries using code, text snippets and natural language to find matches that our AI-driven intent interpretation engine finds semantically similar. The output of search queries is not restricted to exact matches and allows for the discovery of vulnerabilities and other issues which otherwise would be difficult to identify due to a lack of foreknowledge of what to look for.
A recent example of this in the news would be:
“a script embedded in an nginx configuration setting”
Running this search using NLP quickly returns vulnerable code.
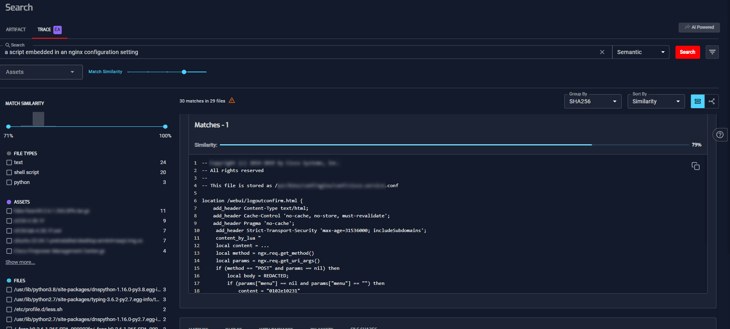
Then we have the ability to research and validate with deterministic checks to ensure this code is truly vulnerable and not a false positive by running it through against CWEs (Common Weakness Enumeration) and OWASP Top 10 best practices.
Trace does not stop there; it lets you quickly and easily visualize all the locations where the weakness exists and the supply chain responsible for them.
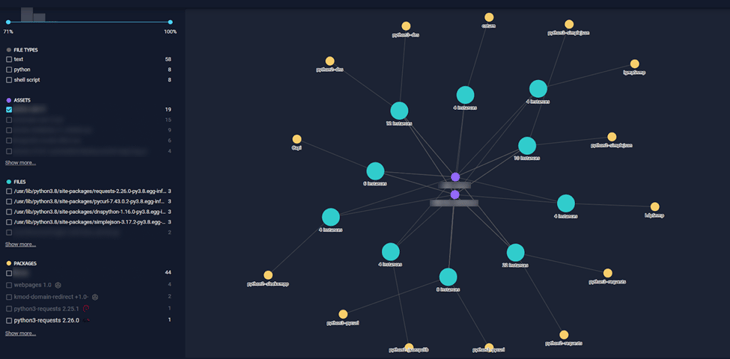
Why it Matters
NetRise Trace is not only immensely useful for finding zero-days and the components associated with them, but also aids efforts to ferret out flaws in code, text files, and configurations. The ability to search across all devices in the NetRise Platform in a manner not unlike the way we have used search engines for the past 20+ years opens up new possibilities for efficiency and effectiveness in vulnerability identification and management. Tracking down firmware and software component security issues quickly and easily with natural language queries enables rapid and precise response to exposures. When a vulnerability is disclosed, NetRise users can immediately identify and take steps to mitigate the threat across their entire environment using a simple search query for the vulnerability. This capability saves organizations time, effort, and money on what would otherwise be a highly time consuming and tedious task in situations where it may become a race between exploiters and the exploitable.
With software supply chain attacks increasing in commonality and frequency year over year, having the rapid response capabilities of the NetRise Platform — and crucially the AI search capability provided by Trace — gives cyber defenders a crucial advantage in the never-ending siege we all find ourselves entrenched in.
Stay up to date with the news
Sign Up To Get Our Free Insights Delivered To Your Inbox




