Introducing Trace: AI Powered Semantic Search for the NetRise Platform
A New Approach to an Old Problem
Over the past couple of years, NetRise has differentiated itself from the rest of the Software Supply Chain Security market with its inside-out approach to cybersecurity. By focusing on the undiscovered and unaddressed vulnerabilities and risks within firmware and software components, NetRise has provided its customers with a solution that comprehensively identifies and prioritizes risk at the most granular level.
While these vital insights are necessary for any vulnerability management program to be truly effective, many have found it difficult to navigate having visibility into such an overwhelming number of previously unknown vulnerabilities. In an effort to increase the real-world utility of the critical information we provide, NetRise has provided risk scoring, remediation recommendations, and the ability to find where else a component or vulnerability is across all devices in an organization. With the release of Trace, we are taking those efforts to the next level.
Introducing NetRise Trace
Trace revolutionizes vulnerability detection and validation for CVEs, CISA KEVs, and more by introducing AI-powered intent-driven searches, allowing users to search their assets based on the underlying motives or purposes behind the code and configurations rather than solely relying on signature-based methods.
Trace enables users to query the entire system based on the intent of malicious actors or negligent developers instead of searching for specific code patterns or known vulnerabilities. This method discovers a wider range of software packages, misconfigurations, or unidentified flaws and allows for highly effective and surprising results. Trace highlights affected assets, files, and packages utilizing natural language, mapping their intricate relationships across the entire software supply chain without the need for a scanning mechanism.
Supply chain compromises are increasingly common, with attackers targeting firmware or open-source software packages through a variety of methods. A widespread effort across industries, involving both public and private sectors, is already underway in the hope of discerning which assets, devices, and software contain compromised software packages and vulnerabilities. The complexity of analyzing device firmware and build artifacts makes these challenges even more difficult.
NetRise addresses these challenges by enabling organizations to quickly trace all impacted assets using a single query. Upon identifying a positive match, it generates a comprehensive graph of the affected software supply chain components, eliminating the need for repeated scans or asset reprocessing. This approach is essential in discerning the extent of threats across devices, firmware, and software packages.
How Does Trace Work?
Trace uses Text Embedding technology to create a representation of humans' natural language a computer can understand and operate on. Essentially, text embeddings allow computers to understand the “intent” of a particular script, block of code, or text file. The Natural Language Processing (NLP) capability of Trace allows a human to ask questions in ways we understand, which Trace can quickly and intelligently interpret to seek out similar results in either meaning or intent.
When the NetRise Platform extracts and analyzes an asset it automatically generates text embeddings for all Python, shell script, and plain text files. Once text embeddings have been generated, users can query their assets using code snippets and natural language to find matches ranked by the similarity percentage. It is designed to allow users to easily find vulnerable coding practices, risky configurations, and other text blocks that may be interesting to the user.
Trace search results are returned as blocks of text within each unique file so users can easily see the affected parts of the file even if that file exists in different locations on multiple assets. Trace is the first solution to integrate AI-driven semantic search, supply chain impact analysis, and vulnerability validation by utilizing large language model (LLM) capabilities. The resulting solution offers customers a unified and potent method for detecting known and hidden threats in low-level firmware and other cyber-physical systems.
Real World Example
Using natural language a user can search for common coding bad practices such as:
“A Python network socket is created and connects to a system which can then send data to /bin/bash”
“Python retrieving user data and passing it directly to the ‘exec’ function”
“A hardcoded JSON Web Token (JWT) is found in a file which can be abused by malicious actors”
Trace then searches through the data that has been indexed and returns code that matches the intent of the search.
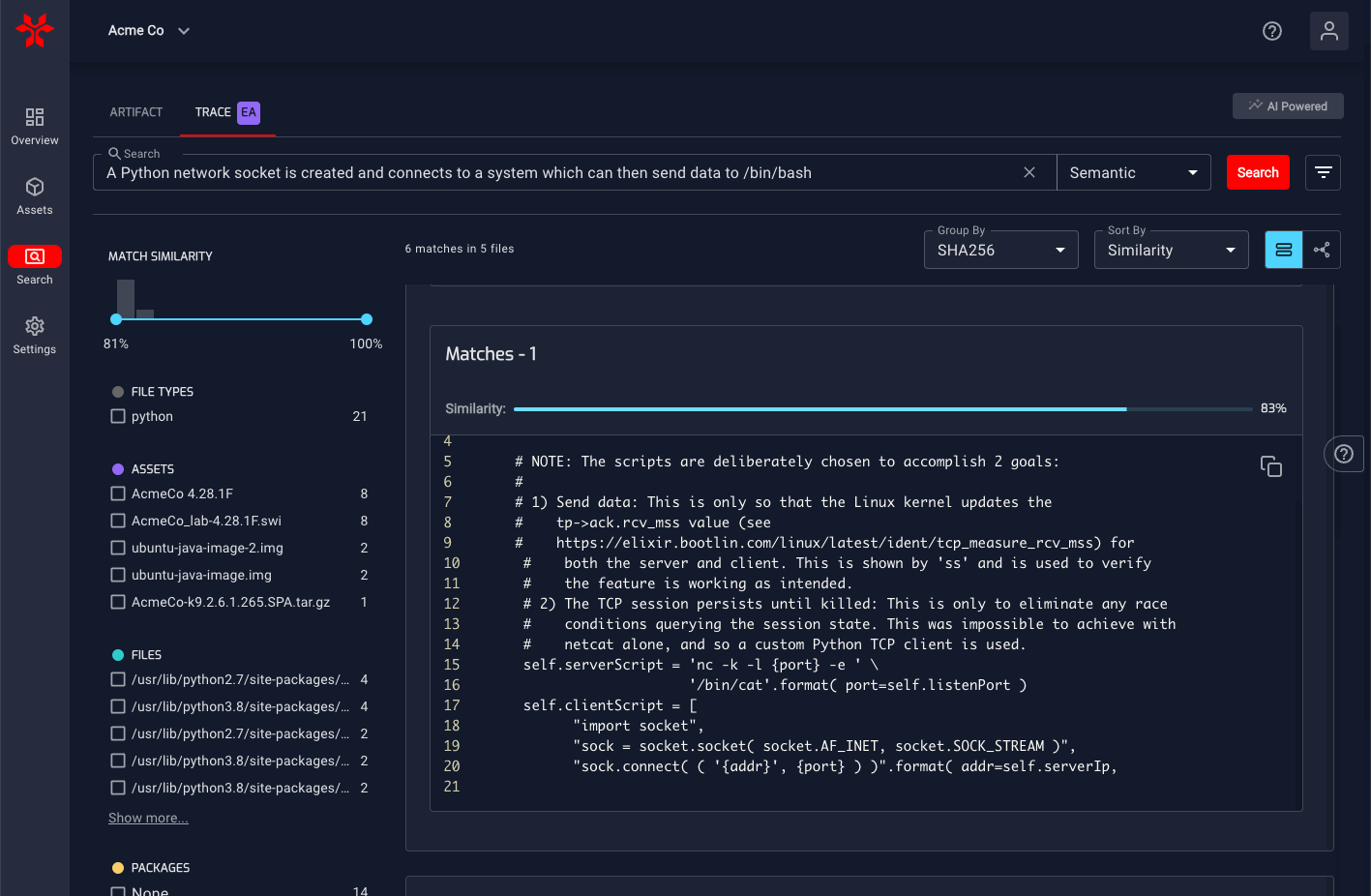
Example Trace Search
.png?width=1316&height=186&name=image%20(5).png)
After the search is complete you can easily see the segment of code that matches the intent being searched for and how similar the results are. We also provide the ability to further refine the search results by specific file, asset types, and level of intent similarity.
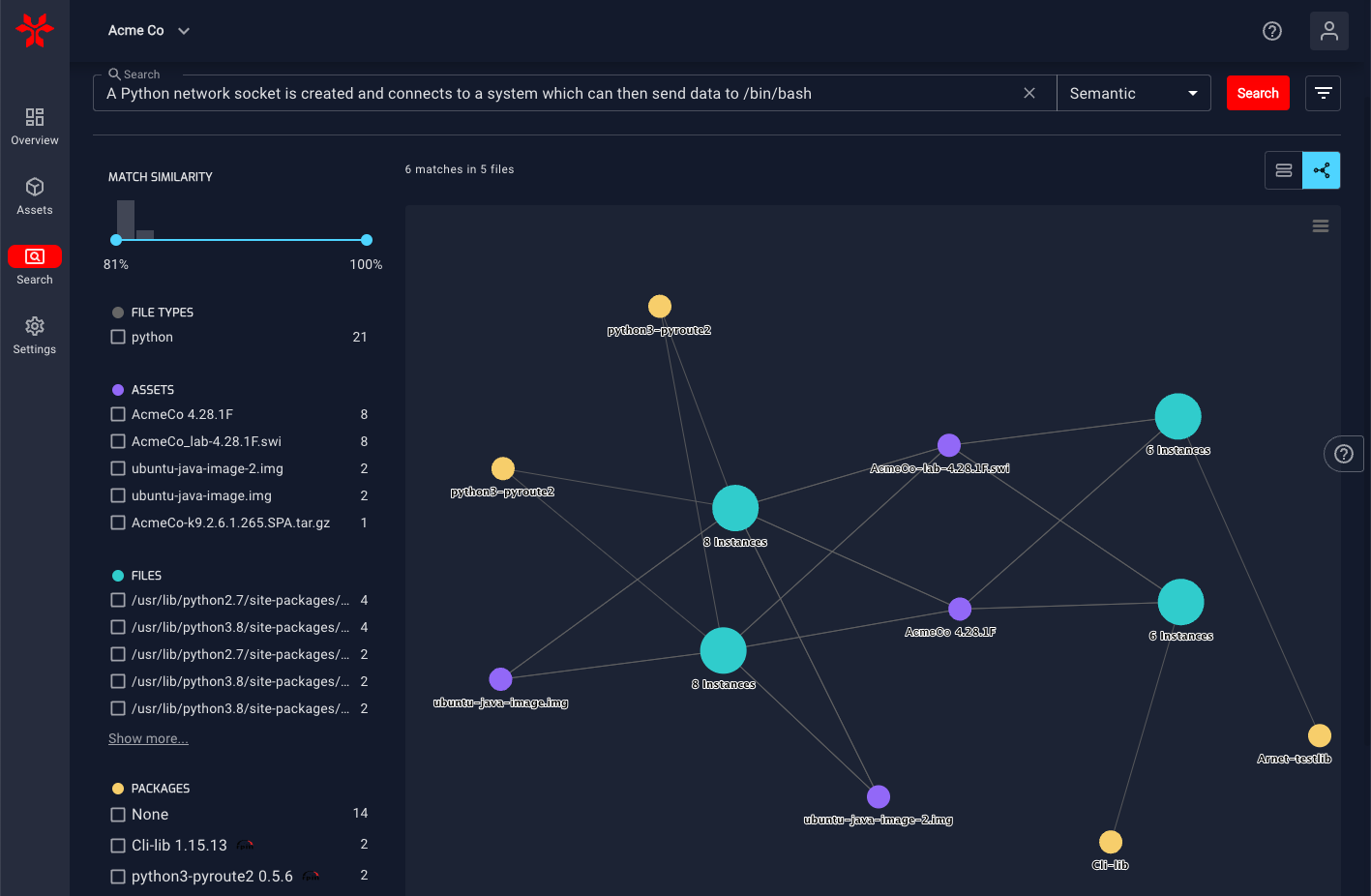
Last but not least, we provide the ability to easily see the supply chain relationships of files, packages and assets in a graph view. This makes it easy to see the sources and impacts of a vulnerable piece of code.
Key Benefits
Key enhancements and capabilities of the new Trace solution in the NetRise Platform include:
- AI-Powered Search: Semantic and keyword-based search for all files, operating system configurations, and vulnerabilities across all assets using AI.
- Deep Supply Chain Introspection & Origin Tracing: Discover and trace the origin of code and risk back to the third-party or proprietary software packages that introduced it across all assets.
- LLM-Based Vulnerability Discovery & Validation: Identify vulnerabilities and gauge their impact in the software supply chain using code-based or broad natural language queries, validating issues across an organization's firmware, software, and cyber-physical systems.
- Visualize Supply Chain Risks: Easily view the relationship between vulnerable code, files, packages, and assets with the NetRise Supply Chain Graph View.
To find out more about NetRise Trace, you can read our press release announcing the new solution or check out the Trace Solution Brief.
To see Trace and the rest of the NetRise Platform in action for yourself, request a demo today.
Stay up to date with the news
Sign Up To Get Our Free Insights Delivered To Your Inbox
You might also like
Explore other exciting events!




