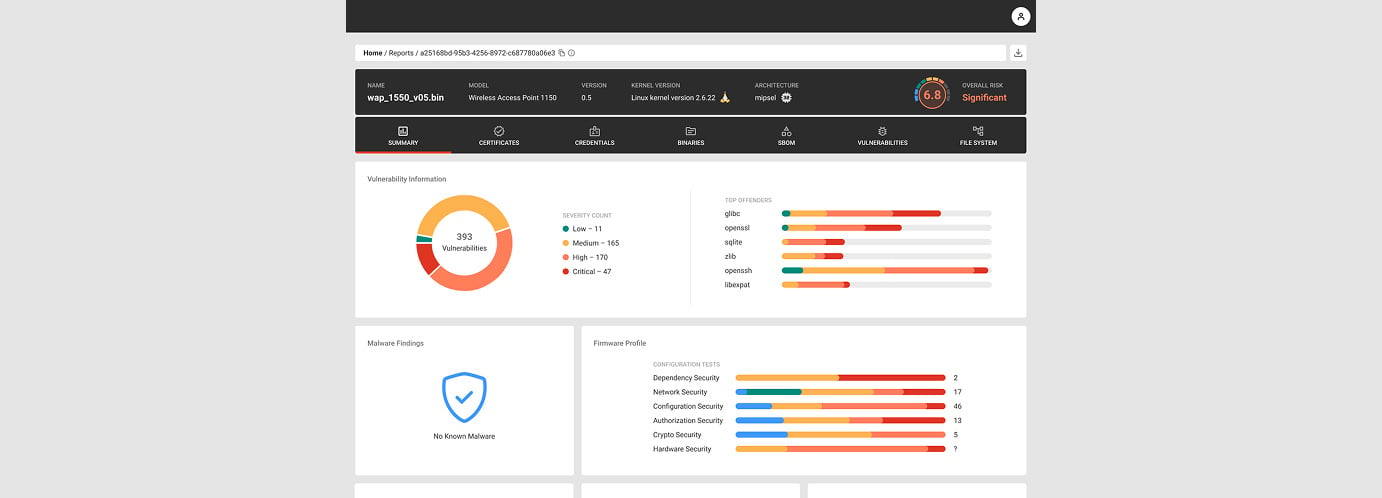
Continuously Monitor for the Latest Risks & Vulnerabilities
The longer a vulnerability or risk is present in your environment, the greater your exposure.
UPDATE & REMEDIATEAutomated, Autonomous Threat Intelligence Monitoring
Time matters when dealing with vulnerabilities and threats. The potential for impact grows greater and greater the longer a vulnerability remains unaddressed in your environment.
The NetRise Platform identifies risks and vulnerabilities in near-real time and scores them based on the likelihood of exploitation and impact. NetRise Trace provides AI-powered semantic searches, enabling users to look for assets based on the motives behind code and configurations rather than relying on traditional signature-based methods.
With NetRise, you get peace of mind knowing:
- Your devices are constantly assessed for the latest risks
- Your security team receives real-time updates when new threats are found
- Identifying affected devices when new threats emerge is quick and easy
- Your team can focus on higher-value tasks instead of manually tracking risks
How It WorksIdentifying Risks
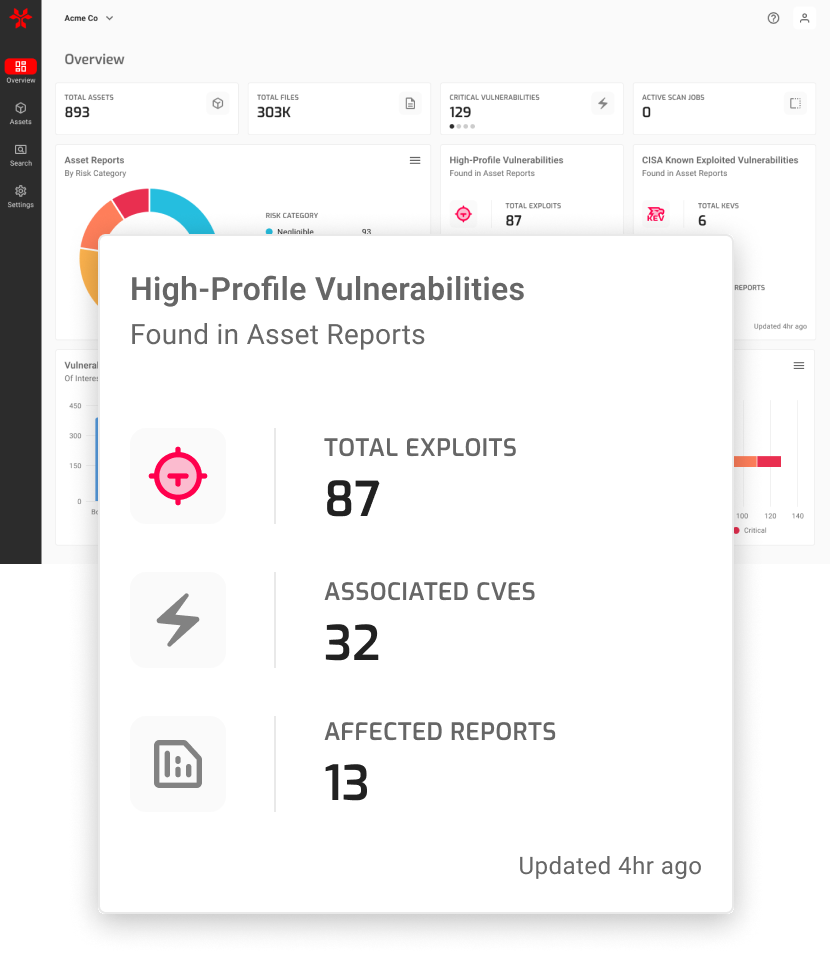
The NetRise Platform goes beyond Common Vulnerabilities and Exposures (CVEs), autonomously identifying and prioritizing risks based on data from the National Vulnerability Database (NVD), the CISA Known Exploited Vulnerabilities Catalog (KEV), Threat Actor Groups, BOTNETs, and more.
The NetRise Platform will alert your security team and highlight the risks with the greatest impact on cybersecurity. We’ll help you understand your risks and recommend a path to remediation. Use NetRise Trace to surface risks you didn't know to look for with AI-powered interpretation of the intent of natural language queries.

BenefitsImprove Risk & Vulnerability Management
Gain a constantly updated understanding of the risk present in your devices and go beyond basic CVE tracking.
Risk Tracking
Quickly determine your exposure and identify unknown risks with NetRise Trace.
Risk Remediation
Cut through the noise to focus on the threats that matter most.
Risk Reduction
Rapidly move from understanding your exposure to mitigation.
Protect Your AssetsSoftware Supply Chain Security for Your Industry
NetRise empowers software supply chain risk management for a variety of industries and operating environments.
Consulting Firms
Partnering with NetRise to investigate firmware is a force multiplier for consultancies. Instead of manually testing the security of XIoT devices, NetRise automates and standardizes the process while producing previously unattainable results. Learn more.
Device Manufacturers
The NetRise Platform enables device manufacturers to find issues in software and firmware before release to customers. NetRise also helps manufacturers quickly investigate and react to vulnerabilities and zero days. Learn more.
Enterprise Corporations
The NetRise Platform makes the opaque inner workings of firmware and software components transparent, providing deep visibility with the most complete SBOMs and the most comprehensive SBOM capabilities of any solution. NetRise provides a central repository for vulnerability management, enabling users to quickly search across every device and vendor. Learn more.
Government Organizations
Devices with unknown risks and unknown supply chains should not be allowed on government networks. Understanding the makeup and risks of devices is critical to secure operations on federal networks. The NetRise Platform aligns directly with executive orders, NERC-CIP, and government standards. Learn more.
Healthcare
NetRise helps healthcare systems stay FDA- and HIPAA-compliant by illuminating vulnerable components in software supply chains and within devices on clinical networks. Learn more.
Power and Utilities
Introducing a device to an environment responsible for critical infrastructure demands a complete understanding of the components, supply chain, and risks of the device. NetRise provides insight into devices and helps ensure adherence to NERC-CIP standards. Learn more.
“We had no idea [these vulnerabilities] existed in our environment. Yes, our vulnerability trending had a spike, but half the battle is even knowing you had those vulnerabilities in the first place.”
Marcos Marrero
CISO at H.I.G. Capital
FAQFrequently Asked Questions About Continuous Monitoring
Everything you need to know about continuous monitoring with the NetRise Platform.
Why is continuous monitoring important?
Time matters when dealing with vulnerabilities and threats in your environment. The longer a vulnerability or risk is present, the greater your exposure to bad actors. Your team doesn’t have time to monitor intelligence threats all day. The NetRise Platform does it all for you and alerts you to threats.
Why do I need NetRise for my XIoT devices?
When you know what components are in your devices, you’re able to mitigate risk better. During events like the log4j breach, IoT device manufacturers and device owners became acutely aware of their inability to determine where vulnerable components are present on networks. A complete component list (a software bill of materials) is the only way to tell if you are exposed to such a vulnerability. NetRise goes beyond simply providing the most complete SBOMs, however. Users can also easily search for vulnerable components across the entire network and quickly determine which devices require attention.
How does NetRise continuous monitoring work?
NetRise monitors the NVD, CISA KEV catalog, Threat Actor Groups, BOTNETs, and more to continuously assess the risks and vulnerabilities within devices. Commonly overlooked risk factors like cracked credentials and misconfigurations are also factored in — enabling organizations to take the most effective next steps first when seeking to mitigate risks and bolster cybersecurity.
Learn MoreNetRise Blog Library
Find more resources about XIoT cybersecurity in our blog.
Ready to See the NetRise Platform?
NetRise is an automated, cloud-based platform that provides comprehensive insight into the
many risks present in firmware and software components.