Using EPSS to Modernize Vulnerability Prioritization
Recent years have seen a record number of Common Vulnerability Enumerations (CVEs) published leaving already overwhelmed security teams with more vulnerabilities to review and prioritize. Historically, these teams have been ill-equipped to make informed decisions about which vulnerabilities they should care about the most or they have been understaffed which prevents them from responding in a timely manner.
To help address these issues, various tools have been developed to aid security teams with vulnerability prioritization. The Common Vulnerability Scoring System (CVSS) is perhaps the most well-known of these. By detailing a vulnerability’s impact to confidentiality, integrity, and availability as well as its attack complexity and vectors, CVSS has been the de facto metric for estimating how much attention should be paid to a particular vulnerability. CVSS was not designed, however, to explain how likely it is for a malicious actor to actively exploit the vulnerability. This creates a problem for security teams: why focus energy and resources on investigating a vulnerability that may never actually be exploited by a malicious actor?
Introduction to EPSS
The Exploit Prediction Scoring System (EPSS), developed by the Forum of Incident Response and Security Teams (FIRST) – the same organization behind CVSS – aims to help solve this problem. Instead of measuring a CVE’s impact, it leverages current, real-world exploit and threat information from many sources to estimate the probability of a vulnerability being exploited in the next 30 days.
Using this information, EPSS then assigns two values to each CVE; a probability and a percentage, each ranging from a possible score of 0.0 to 1.0 (0% to 100%). The probability score represents the probability of the CVE being exploited by malicious actors in the next 30 days. The percentage score represents the likelihood in the context of all other vulnerabilities.
An important trait of EPSS scores that may be unfamiliar to some teams is that they are updated on a daily basis. Estimating the probability of exploitation requires frequent data updates because malicious actors are constantly updating their techniques and targeting different vulnerabilities in order to evade the latest defenses.
Organizations who are looking to make use of EPSS should keep this requirement in mind because data can change dramatically on a daily basis. This may be unexpected because other tools, like CVSS, are very rarely updated because their nature does not require it. Frequent data updates are ultimately a positive addition to an organization’s tool set but may require process changes or additional requirements.
Leveraging EPSS for Effective Prioritization
EPSS can be used in various ways, either as a standalone tool or in conjunction with other vulnerability data sources such as CVSS and the Cybersecurity and Infrastructure Security Agency (CISA) Known Exploited Vulnerabilities (KEV) Catalog. While CVSS provides valuable information about the impact of a vulnerability, it does not necessarily reflect its likelihood of exploitation. This is where EPSS shines, offering a complementary perspective that helps paint a more complete picture of vulnerabilities that an organization should focus on.
To illustrate this, take a look at the chart below taken from FIRST’s website with our additions of the red “quadrant” lines:
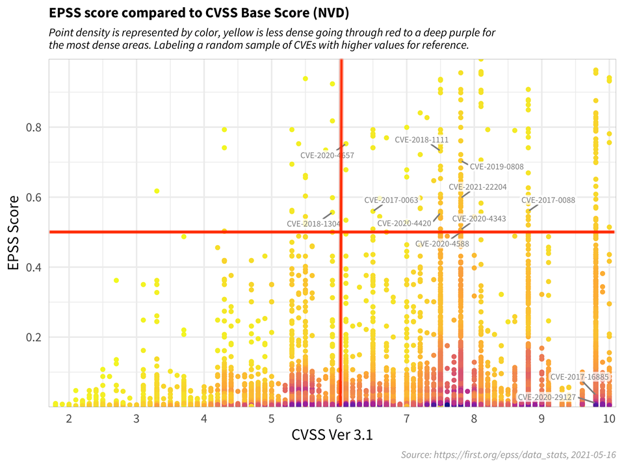
Notice the massive number of vulnerabilities (the red and purple dots) in the bottom two quadrants of the chart. These represent all of the vulnerabilities that have very low probabilities of being exploited. This is important because it is direct evidence that just because a vulnerability has a high CVSS score does not imply that it will be utilized by a malicious actor.
Also notice that the number of vulnerabilities gets dramatically smaller as the EPSS score (the Y-axis) goes up. By prioritizing the vulnerabilities that fall into the top right quadrant; those that have a high CVSS score (impact) and high EPSS score (likelihood of exploitability), organizations can go from a list of hundreds or thousands of vulnerabilities down to just a handful to focus on. That isn’t to say that all other vulnerabilities should be ignored but for organizations who are trying to get a handle on their vulnerability management and prioritization processes or are wanting to make the biggest impact on reducing exploitation risk, using a combination of CVSS and EPSS is a great starting point.
This concept of quadrants can be easily adjusted for organizations of all risk profiles. For example, if an organization has a pre-existing policy that states they will “prioritize and review CVES with a CVSS of 7 or higher”, the team will effectively be shrinking the top right quadrant which will further help with prioritization. This method can also highlight CVEs of a similar risk (e.g. a 6.5 CVSS score) that may be highly likely to be exploited but would not have been prioritized under the pre-existing policy.
No vulnerability scoring system will be perfect for every organization out of the box. EPSS requires data surrounding a vulnerability which sometimes does not exist especially when the details of a vulnerability are first released. It also relies on machine learning and the creation and maintenance of models for the scoring methodology. Although the models are public there does not appear to be formal oversight around the maintenance of the models. It also lacks one of the most difficult to measure and track metrics of a vulnerability - the business impact of the asset if it were to be compromised.
To further enhance vulnerability prioritization, organizations can overlay this data with information from additional sources, the CISA KEV Catalog, for example. Remember, EPSS is an estimated probability of a vulnerability being exploited which means that sometimes it will be wrong. A vulnerability with a high score may go unexploited or a low score may end up being leveraged. Adding CISA KEV into the mix allows organizations to add a “direct evidence of exploitation” signal to their prioritization which can help validate when EPSS is correct and act as a safety net when it is not.
Conclusion
As malicious actors continue to rapidly change their techniques, the need for effective vulnerability prioritization has never been greater. By using EPSS, organizations can gain valuable insight into the likelihood of exploitation and make informed decisions about where to focus their efforts. By combining EPSS with other data sources such as CVSS and CISA KEV, security teams can create a comprehensive vulnerability management strategy that minimizes risk and strengthens overall cybersecurity posture.
The NetRise Platform does this analysis and prioritization automatically and presents users with the vulnerabilities grouped into priority categories that map to each of the quadrants discussed above. For example, vulnerabilities that are in the CISA KEV Catalog will bubble up to Priority 1, the highest priority. Vulnerabilities that have an EPSS score greater than 0.2 and a CVSS score greater than or equal to 6 will be grouped into Priority 2 which represents the top right quadrant. An EPSS score less than 0.2 and CVSS greater than or equal to 6 is Priority 3 or the bottom right quadrant. An EPSS greater than 0.2 and CVSS less than 6 is Priority 4. Finally an EPSS less than 0.2 and CVSS less than 6 is Priority 5.
Reach out for a demo today to learn about the other ways that the NetRise Platform can help you discover and manage risk in your XIoT devices.
Stay up to date with the news
Sign Up To Get Our Free Insights Delivered To Your Inbox




