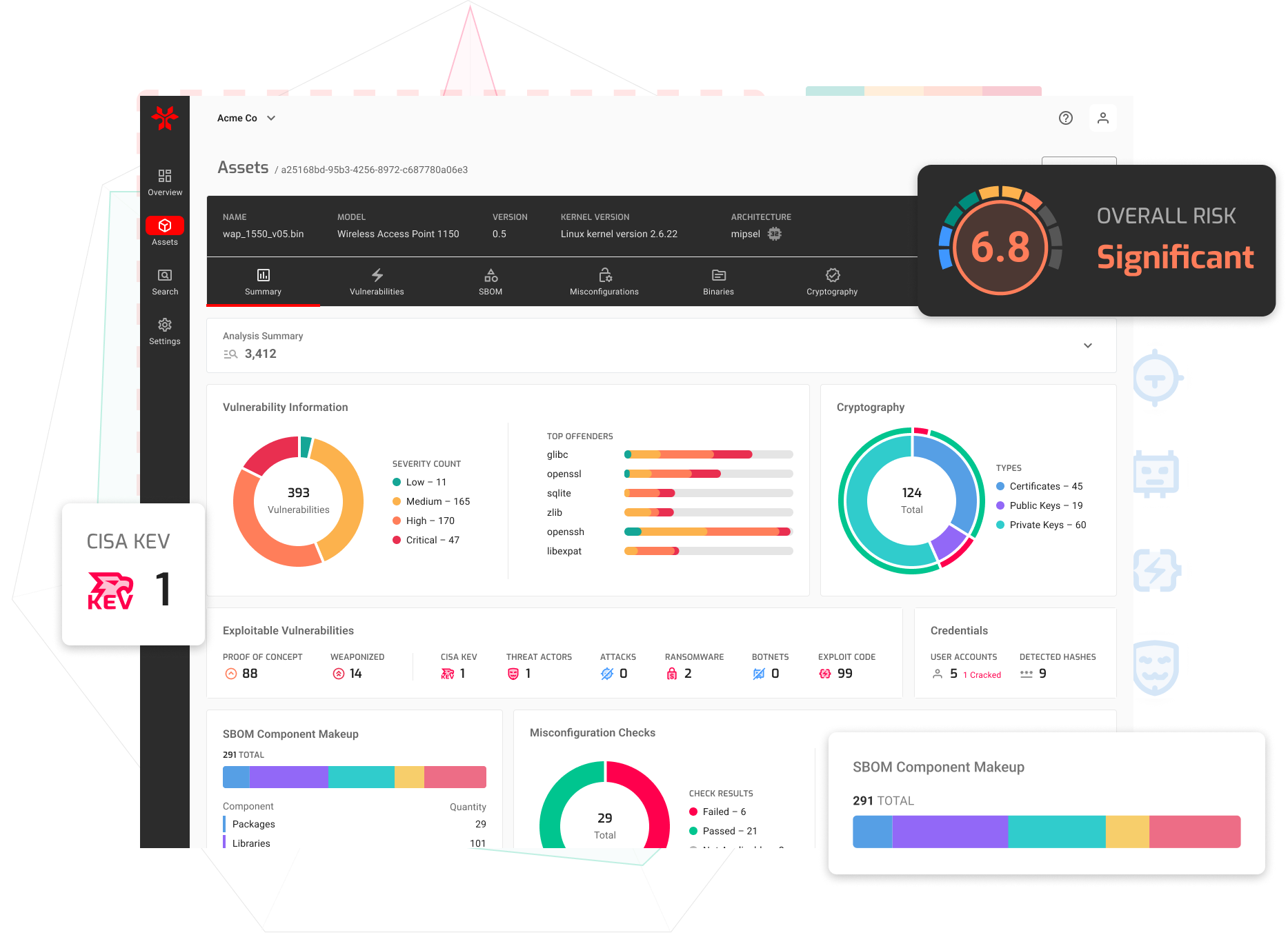
Security & Privacy at NetRise
As a leader in Software Supply Chain Security, our own security and compliance is foundational to our customer’s success.
Governance
NetRise’s internal security and privacy experts establish policies and controls, monitor compliance with controls, and routinely undertake independent assessments of our security and compliance. Our policies and controls are founded on the following principles:
Access Control
Access is granted on the basis of least privilege and administrative or role based access to the NetRise platform can be secured with MFA.
Implementation
Security controls are implemented and layered in alignment with a defense-in-depth approach.
Consistency
Security controls are applied consistently to all areas of the organization.
Iteration
The implementation of controls is an iterative process, seeking to continuously improve effectiveness and auditability while decreasing friction.

Security & Compliance
NetRise maintains compliance with all applicable government regulations and appropriate frameworks, including SOC 2 Type II.
For more details on our internal security practices, please review our Terms of Service or reach out to your NetRise account manager.
For more information on how collected data is handled, please see our Privacy Policy.
Data Protection
All stored customer data is encrypted and segmented using GCS (Google Cloud Storage) best practices. Row-level encryption is also applied to sensitive collections and tables. Data is encrypted even before it reaches the database, ensuring neither physical access nor logical access to the database is sufficient to interpret sensitive information.

In any instance where data must be transferred over potentially insecure networks, NetRise utilizes TLS 1.2 or higher. Features such as HSTS (HTTP Strict Transport Security) are also employed to maximize the security of data in transit. Server TLS keys and certificates are managed by GCP and deployed via Application Load Balancers.

Encryption keys are managed via GCP Cloud Key Management System (KMS). KMS stores key material in Hardware Security Modules (HSMs), which prevents direct access by any individuals, including employees of Google and NetRise. The keys stored in HSMs are used for encryption and decryption via Google KMS APIs. Application secrets are encrypted and stored securely via GCP Secrets Manager and access to these values is strictly limited.

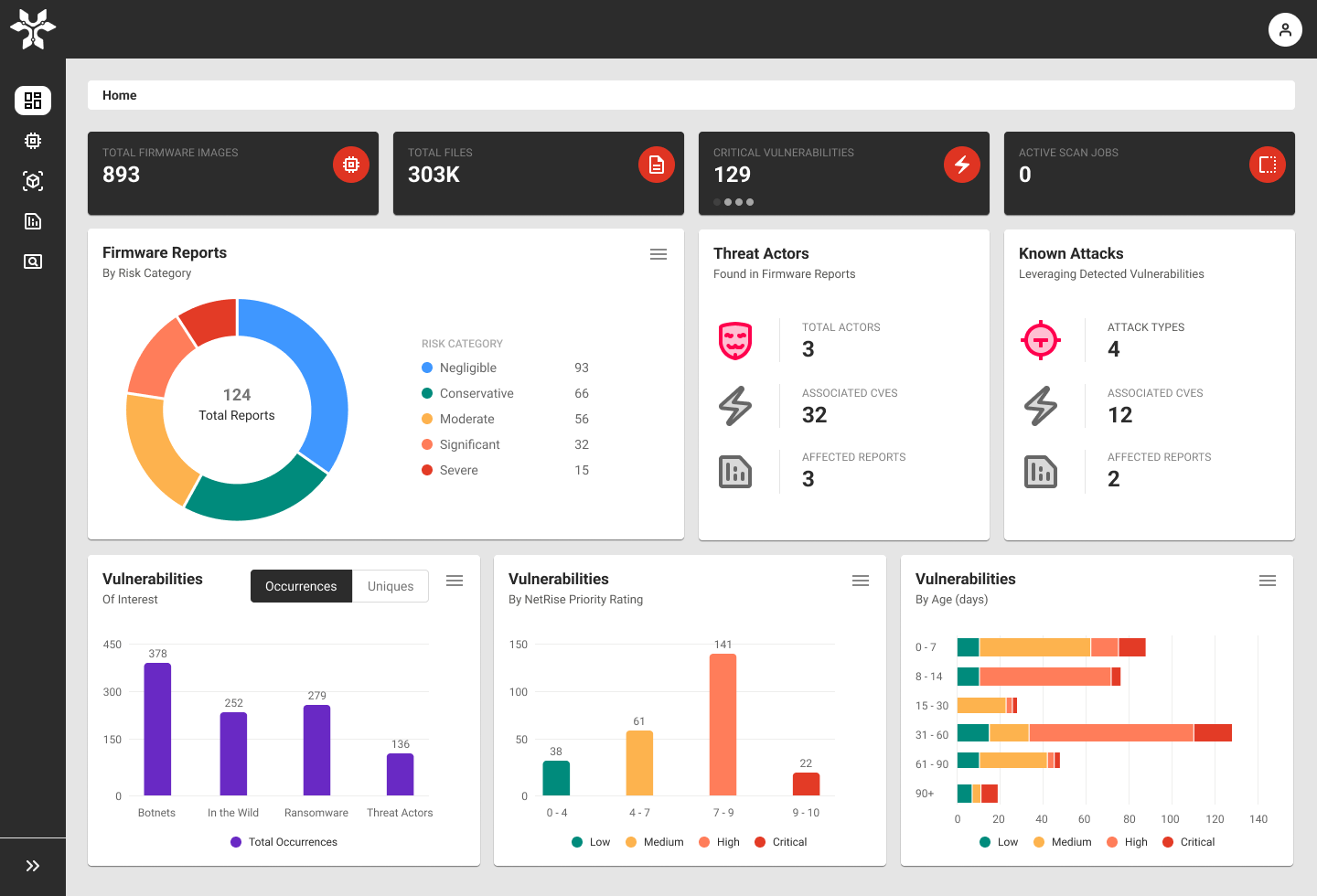
Product & Enterprise Security
Penetration Testing
NetRise engages with one of the best penetration testing consulting firms in the industry at least annually. All areas of the NetRise product and cloud infrastructure are in-scope for these assessments, and source code is fully available to the testers in order to maximize the effectiveness and coverage.
Vulnerability Assessment
NetRise requires vulnerability assessments at key stages of our Secure Development Lifecycle (SDLC):
- Static analysis (SAST) testing of code during pull requests and on an ongoing basis
- Software composition analysis (SCA) to identify known vulnerabilities in our software supply chain
- Malicious dependency scanning to prevent the introduction of malware into our software supply chain
- Dynamic analysis (DAST) of running applications
- Periodic network vulnerability scanning
- Continuous external attack surface management (EASM) to discover new external-facing assets
Endpoint Protection
All corporate devices are centrally managed and equipped with mobile device management and anti-malware protection. Endpoint security alerts are monitored 24/7/365. MDM is used to enforce secure configuration of endpoints, such as disk encryption, screen lock configuration, and software updates.
Vendor Security
NetRise uses a risk-based approach to vendor security. Factors which influence the inherent risk rating of a vendor include:
- Access to customer and corporate data
- Integration with production environments
- Potential damage to the NetRise brand
Once the inherent risk rating has been determined, the security of the vendor is evaluated in order to determine a residual risk rating and an approval decision for the vendor.
Responsible Disclosure
Want to report an issue? Contact us at security@netrise.io.

