See Why You Have a
False Sense of
Security
A new NetRise report indicates that SBOMs from source-code analysis miss vulnerabilities that are introduced in the build, endangering your software supply chain security.
Static
Linking
can introduce vulnerable library versions unexpectedly.
Build Time
Dependency
Resolution
can substitute old versions of libraries with vulnerable code.
Transitive
Dependencies
at Compilation
can pull in old modules when your scanner can no longer tell.
Vendored
Dependencies
introduced by third-party libraries to ensure compatibility are hidden
Your Security Scans Are Missing Critical Vulnerabilities that only Binary Analysis Can Find
There's a gap - a false sense of security - that exists after you've completed your source-code analysis.
The build process often introduces components that your developers aren't aware of.
For Product Security Leaders
Reduce reputational risk and reliably deliver secure products with binary software composition analysis before you ship.
For Third Party Risk Managers
Verify the accuracy of your vendors' SBOMs to give you the upper hand in negotiations.
For CISOs
Report to your board how you've reduced risk by closing the gap left by source-code analysis.
Learn How To Secure Your Software Supply Chain to End Your False Sense of Security
FREE ANALYST REPORT - NO FORM FILL
Your Security Scans Are Missing Critical Vulnerabilities Here's Why. . .
- Understand the hidden attack surface caused by stating linking during build
- Learn how to investigate unexpected findings to secure your products
- Here's some tough love: you don't know what you're shipping or what you're buying

Continuous Monitoring for Supply Chain Risk
Supply chain risk changes daily. NetRise provides ongoing monitoring across your devices and vendors, alerting you when new vulnerabilities or misconfigurations appear so you can respond quickly.
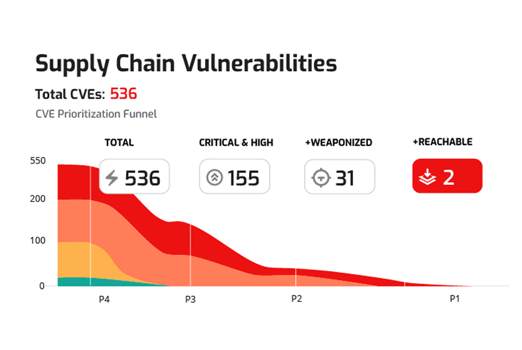
Enriched Vulnerability Context and Prioritization
Finding flaws is only half the battle. NetRise provides context on known exploits, reachable through the network, and in components that autorun at startup so that your team can prioritize findings.
.png?width=687&height=444&name=Rectangle%20161125835%20(1).png)
Request A Personalized Demo
See how NetRise uses binary analysis to uncover hidden vulnerabilities, enrich
SBOMs, and simplify compliance with actionable visibility.
.png?width=112&height=112&name=image%207%20(5).png)




